Black Magic Probe
There are many JTAG and SWD debuggers available for the ARM Cortex-M4 processor. We have had good results using the Black Magic Probe from Black Sphere Technologies.
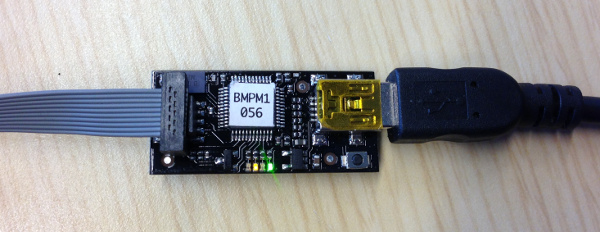
Black Magic Probe
PX4 Autopilot Project Guide
As your primary resource, please read the Black Magic Probe project wiki.
Upgrading Firmware
We’ve found that some Black Magic Probes do not ship with the very latest firmware. In order to support the PX4FMU’s STM32F4 processor, we recommend to follow the instructions on the Black Magic Probe wiki to clone and build the latest black magic firmware and load it on your device.
GDB Init Script
Copy the following to a .gdbinit script in the root directory of your smaccmpilot-stm32f4 repository:
target extended SERIAL_PORT
monitor swdp_scan
attach 1where SERIAL_PORT is the path of the first serial device enumerated by the Black Magic probe.
Using GDB
From the root of the smaccmpilot-stm32f4 repository, after successfully building the SMACCMPilot executable, start your ARM toolchain gdb with the flight executable.
arm-none-eabi-gdb platform-fmu24/standalone-flight/image
If you’ve created the .gdbinit script above, you are now ready to load and run the SMACCMPilot application. If not, you may enter those commands sequentially at the gdb prompt.
Once your gdb is attached to the probe, you can write the program to flash with the command:
(gdb) loadThen, to begin execution, use the command:
(gdb) runOther GDB Resources
Your author typically uses this gdb reference card while debugging.